Cerber and Locky are two the most common ransomwares out in the wild today. Recently, the authors of have launched new variants to the wild simultaneously as an early holiday gift. The new ransomware versions released perform slight, but interesting changes that may affect the way they are being detected.
CERBER 5.0
The creators behind Cerber, like other creators in the ransomware industry, innovate on a daily basis. Researchers detected on November 23rd, 2016, that a new version of Cerber was released (4.1.6). However no prominent changes were noticed in it. Then, less than 24 hours later, the creators behind Cerber released another new version, dubbed 5.0.
The notable change introduced in Cerber version 5, is the use of new IP ranges used for command and control communication. Cerber 5.0 continues to use one IP range which was also used in its last version (4.1.6), while the rest of the IP ranges are new.
The new IP ranges are as follows:
- 194.165.17.0/24
- 194.165.18.0/24
- 194.165.19.0/24
- 15.93.12.0/27
- 63.55.11.0/27
The old IP range still in use:
- 194.165.16.0/24
As in previous versions, Cerber broadcasts messages to all IP addresses in the above-mentioned ranges via UDP. The message that starts the communication is the regex: “hi(0-9){4}b(0-9){3}”.
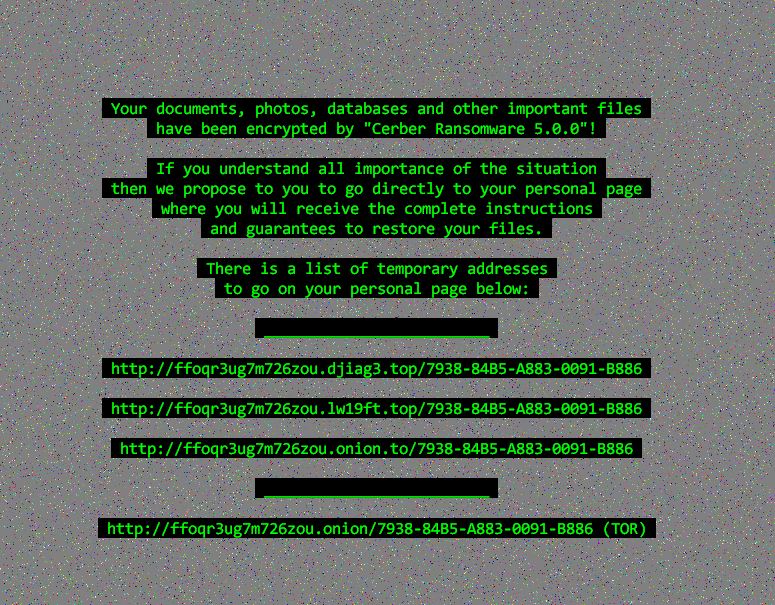
Cerber is distributed via spam e-mail campaigns and exploit kits, specifically Rig-V Exploit Kit. Encrypted file extensions are randomly generated in the same matter as in Cerber’s latest versions, using 4 random alphabetic letters. Cerber 5.0 remains focused on databases and files related to it, encrypting many different types of database file types. In addition, Cerber 5.0 informs users which version of the ransomware they’ve been encrypted by, via its desktop ransom note:
On top of that, researchers have found decryption instructions appear in an interactive .hta file, with information in different languages as it appears that creators are attempting to localize the ransomware to expand their target audience.
LOCKY
The continuously mutating Locky ransomware was released as new variant which implements new evasion techniques and adjusted ransom tariff. Locky is known for being downloaded as a .dll file using JavaScript based downloader. Although the new variant acts just the same, the JavaScript downloader pulls down a disguised .TDB file which turns out to be a PE file. Locky’s creator does this in an attempt to evade security products that have previously identify the infection chain.
As in all recent releases, Locky changed the encrypted files extension, however this time to .zzzzz.
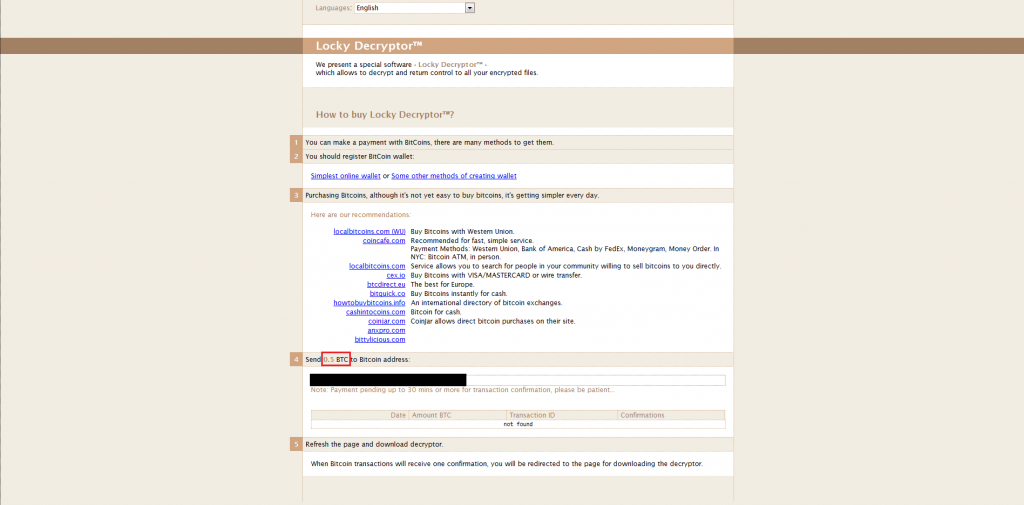
Another behavior is the variable ransom payment. Researchers have noticed that the default requested payment is 3 Bitcoins ($2,260.50 USD); however, when letting the malware communicate with its command and control, the payment amount may change in correlation to the victim’s profile which is based on the number of files it encrypted. The lowest amount that has been demanded in our labs was 0.5 Bitcoin ($376.75 USD). Locky continues to provide the victim with a helpful list of URL’s which can be used to purchase the required Bitcoin payment.
The creators of the Cerber and Locky ransomware constantly are adapting to the security vendors’ counter-measures. While Cerber 5.0 and Locky’s .zzzzz are the ransomwares’ current versions, it is highly unlikely to be their last. Security professionals, businesses and consumers need to be vigilant in the fight against the ransomware epidemic. By leveraging proactive prevention software like Cylance Protect, you can be assured that variants of known ransomware like Cerber and Locky will not impact your computer systems or networks.