Disinformation, Fortify 24x7 Team, News
Cybersecurity News & Resources You Need To Assess Current Threats
The Beers & Bytes Podcast
When you're thirsty for cheesy entertainment AND information security, grab a beer and the latest episode of Beers & Bytes. 
Sorry, no posts found.
All
LatestSchneider Electric Trio Q Licensed Data Radio
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 5.4 ATTENTION: Low attack complexity Vendor: Schneider Electric Equipment: Trio Q Licensed Data Radio Vulnerabilities: Insecure Storage of Sensitive Information, Initialization of a...
CVE Notifications
PopularCVE-2020-9395
An issue was discovered on Realtek RTL8195AM, RTL8711AM, RTL8711AF, and RTL8710AF devices before 2.0.6. A stack-based buffer overflow exists in the client code that takes care of WPA2’s 4-way-handshake via a malformed...
CERT Insider Threats
LatestUEFI – Terra Firma for Attackers
This blog post focuses on how the vulnerabilities in firmware popularized by the Uniform Extensible Firmware Interface create a lucrative target for high-profile attackers.
Ashley Madison To Pay Millions In Breach Settlement
Ashley Madison and New York Attorney General Schneiderman Announces $17.5 Million Settlement In Joint Multi-State And FTC Agreement. The settlement follows investigation finding that the adult dating website had lax security...
Read MoreMillions of University Emails for Sale on Dark Web
Researchers have found millions of US University emails (and passwords) for sale on the Dark Web. The stolen email addresses/password combinations are selling for $3.50 – $10 each. This is only a fraction of a lucrative...
Read More
Disinformation
PopularIs hate speech covered by the First Amendment?
SHARE AND INFORM OTHERS:.fusion-body .fusion-builder-column-0{width:100% !important;margin-top : 0px;margin-bottom : 20px;}.fusion-builder-column-0 > .fusion-column-wrapper {padding-top : 0px !important;padding-right : 0px...
CERT-Vulnerabilities, National Cyber Awareness
LatestVU#952657: Rsync contains six vulnerabilities
Overview Rsync, a versatile file-synchronizing tool, contains six vulnerabilities present within versions 3.3.0 and below. Rsync can be used to sync files between remote and local computers, as well as storage devices. The...
SANS ISC Bulletins
LatestZero Trust and Entra ID Conditional Access, (Sun, Jan 19th)
Microsoft Entra ID (Formerly Azure AD) Conditional Access (CA) policies are the key components to a Zero Trust strategy, as it provides the ability to function as the front door for users and devices. CA policies use attributes,...
The Ransomware Epidemic in Healthcare
Ransomware attacks have plagued business of all sizes, healthcare institutions and even government entities during the first half of 2016, forcing CEO’s and CIO’s into damage control mode as IT teams scramble to beef...
Read More
Kicking-Off with a December 4th Workshop, NIST is Revisiting and Revising Foundational Cybersecurity Activities for IoT Device Manufacturers, NIST IR 8259!
In May 2020, NIST published Foundational Cybersecurity Activities for IoT Device Manufacturers (NIST IR 8259), which describes recommended cybersecurity activities that manufacturers should consider performing before their IoT...
Baxter Life2000 Ventilation System
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 10.0 ATTENTION: Exploitable remotely/low attack complexity Vendor: Baxter Equipment: Life2000 Ventilation System Vulnerabilities: Cleartext Transmission of Sensitive Information, Improper...
How to Bring Zero Trust to Wi-Fi Security with a Cloud-based Captive Portal?
Recent data breaches have highlighted the critical need to improve guest Wi-Fi infrastructure security in modern business environments. Organizations face increasing pressure to protect their networks while providing convenient...
Arbitrary file write on GUI
A relative path traversal vulnerability [CWE-23] in FortiManager & FortiAnalyzer may allow a privileged attacker with super-admin profile and CLI access to write files on the underlying system via crafted HTTP or HTTPS...
Fortify Partners with SeedPod to offer Robust Cyber Insurance
SeedPod Cyber, the intelligent cyber insurance company tailored for Managed Service Providers (MSPs) and Managed Fortify24x7...
Schneider Electric PowerChute Serial Shutdown
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 6.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: Schneider Electric Equipment: PowerChute Serial Shutdown Vulnerability: Improper Authentication 2. RISK EVALUATION...
2054 Mass Metrology Seminar
Course Description The Mass Metrology Seminar is a two-week, “hands-on” seminar. It incorporates approximately 30 percent lectures and 70 percent demonstrations and laboratory work in which the participant performs...
ABB ASPECT-Enterprise, NEXUS, and MATRIX Series Products
View CSAF 1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low attack complexity Vendor: ABB Equipment: ASPECT-Enterprise, NEXUS, and MATRIX series Vulnerabilities: Files or Directories Accessible to External...
Data Pipeline Challenges of Privacy-Preserving Federated Learning
This post is part of a series on privacy-preserving federated learning. The series is a collaboration between NIST and the UK government’s Responsible Technology Adoption Unit (RTA), previously known as the Centre for Data...
BD Diagnostic Solutions Products
View CSAF 1. EXECUTIVE SUMMARY CVSS v3 8.0 ATTENTION: Low attack complexity Vendor: Becton, Dickinson and Company (BD) Equipment: Diagnostic Solutions Products Vulnerability: Use of Default Credentials 2. RISK EVALUATION...
New U.S. DoJ Rule Halts Bulk Data Transfers to Adversarial Nations to Protect Privacy
The U.S. Department of Justice (DoJ) has issued a final rule carrying out Executive Order (EO) 14117, which prevents mass transfer of citizens’ personal data to countries of concern such as China (including Hong Kong and...
[FortiWLM] Unauthenticated limited file read vulnerability
A relative path traversal [CWE-23] in FortiWLM may allow a remote unauthenticated attacker to read sensitive files. Revised on 2024-12-18 00:00:00
CISA Adds One Known Exploited Vulnerability to Catalog
CISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2021-44207 Acclaim Systems USAHERDS Use of Hard-Coded Credentials Vulnerability These types of...
11th Annual NICE K12 Cybersecurity Education Conference
The next NICE K12 Cybersecurity Education Conference will take place December 8-9, 2025 in Nashville, Tennessee. This event is supported by NICE, a program of the National Institute of Standards and Technology in the U.S....
Hitachi Energy SDM600
View CSAF 1. EXECUTIVE SUMMARY CVSS v3 8.0 ATTENTION: Exploitable from adjacent network Vendor: Hitachi Energy Equipment: SDM600 Vulnerabilities: Origin Validation Error, Incorrect Authorization 2. RISK EVALUATION Successful...
NIST’s International Cybersecurity and Privacy Engagement Update – New Translations
As the year comes to a close, NIST continues to engage with our international partners to strengthen cybersecurity, including sharing over ten new international translations in over six languages as resources for our...
Christmas “Gift” Delivered Through SSH, (Fri, Dec 20th)
Christmas is at our doors and Attackers use the holiday season to deliver always more and more gifts into our mailboxes! I found this interesting file this morning: “christmas_slab.pdf.lnk”[1]. Link files (.lnk) are...
Ossur Mobile Logic Application
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 5.6 ATTENTION: Low attack complexity Vendor: Ossur Equipment: Mobile Logic Application Vulnerabilities: Exposure of Sensitive System Information to an Unauthorized Control Sphere, Command...
HubPhish Exploits HubSpot Tools to Target 20,000 European Users for Credential Theft
Cybersecurity researchers have disclosed a new phishing campaign that has targeted European companies with an aim to harvest account credentials and take control of the victims’ Microsoft Azure cloud infrastructure. The...
Missing authentication in fgfmsd
A missing authentication for critical function vulnerability [CWE-306] in FortiManager fgfmd daemon may allow a remote unauthenticated attacker to execute arbitrary code or commands via specially crafted requests.Reports have...
Cybersecurity Job Market Stagnates, Dissatisfaction Abounds
The 2024 ISC2 Cybersecurity Workforce Study found that amid a tightening job market and dynamic...
Staff Stories Spotlight Series: Cybersecurity Awareness Month 2024
This blog is part of a larger NIST series during the month of October for Cybersecurity Awareness Month , called ‘Staff Stories Spotlight.’ Throughout the month of October this year, Q&A style blogs will be...
CISA Adds Two Known Exploited Vulnerabilities to Catalog
CISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-20481 Cisco ASA and FTD Denial-of-Service Vulnerability CVE-2024-37383 RoundCube Webmail...
Development Features Enabled in Prodcution, (Thu, Oct 24th)
We do keep seeing attackers “poking around” looking for enabled development features. Developers often use these features and plugins to aid in debugging web applications. But if left behind, they may provide an...
BD Alaris Infusion Central (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.3 ATTENTION: Low attack complexity Vendor: Becton, Dickinson and Company (BD) Equipment: Alaris Infusion Central ——— Begin Update A part 1 of 2 ———...
International Face and Fingerprint Performance Conference (IFPC) 2025
NIST is pleased to announce the IFPC 2025, which is focused on all technical factors affecting the deployment and use of high performance face recognition applications, including applications, standards, risk management, quality...
Chinese Nation-State Hackers APT41 Hit Gambling Sector for Financial Gain
The prolific Chinese nation-state actor known as APT41 (aka Brass Typhoon, Earth Baku, Wicked Panda, or Winnti) has been attributed to a sophisticated cyber attack targeting the gambling and gaming industry. “Over a period...
Kieback&Peter DDC4000 Series
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: Kieback&Peter Equipment: DDC4000 Series Vulnerabilities: Path Traversal, Insufficiently Protected Credentials, Use of...
Iranian Cyber Actors’ Brute Force and Credential Access Activity Compromises Critical Infrastructure Organizations
Summary The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), the Communications Security Establishment Canada (CSE), the Australian Federal...
Priviledged admin able to view device summary for device in different ADOM
An exposure of sensitive information to an unauthorized actor vulnerability [CWE-200] in FortiManager Administrative Domain (ADOM) may allow a remote authenticated attacker assigned to an ADOM to access device summary of other...
North Korea Hackers Get Cash Fast in Linux Cyber Heists
The thieves modify transaction messages to initiate unauthorized withdrawals, even when there are...
Staff Stories Spotlight Series: Cybersecurity Awareness Month 2024
This blog is part of a larger NIST series during the month of October for Cybersecurity Awareness Month , called ‘Staff Stories Spotlight.’ Throughout the month of October this year, Q&A style blogs will be...
CISA Releases Three Industrial Control Systems Advisories
CISA released three Industrial Control Systems (ICS) advisories on October 3, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-24-277-01 TEM...
Survey of CUPS exploit attempts, (Fri, Oct 4th)
It is about a week since the release of the four CUPS remote code execution vulnerabilities. After the vulnerabilities became known, I configured one of our honeypots that watches a larger set of IPs to specifically collect UDP...
Baxter Connex Health Portal
View CSAF 1. EXECUTIVE SUMMARY CVSS v3.1 10.0 ATTENTION: Exploitable remotely/low attack complexity Vendor: Baxter Equipment: Connex Health Portal Vulnerabilities: SQL Injection, Improper Access Control 2. RISK EVALUATION...
AI-Powered Rhadamanthys Stealer Targets Crypto Wallets with Image Recognition
The threat actors behind the Rhadamanthys information stealer have added new advanced features to the malware, including using artificial intelligence (AI) for optical character recognition (OCR) as part of what’s called...
5×5: The Public Safety Innovation Summit
SAVE THE DATE 5×5 ― the confirmation of a strong and clear signal ― and the place to make your voice heard and drive public safety communications forward. In 2025, the FirstNet Authority and the National Institute of...
78 Combined Regional Measurement Assurance Program (C-RMAP)
NIST Handbook 143, Section 5.2, Table 2 notes that annual attendance at the RMAP training session is required for ongoing laboratory Recognition of State weights and measures metrology staff. Handbook 143, Program Handbook...
Atelmo Atemio AM 520 HD Full HD Satellite Receiver
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.3 ATTENTION: Exploitable remotely/low attack complexity/public exploits are available Vendor: Atelmo Equipment: Atemio AM 520 HD Full HD Satellite Receiver Vulnerability: OS Command...
VU#138043: A stack-based overflow vulnerability exists in the Microchip Advanced Software Framework (ASF) implementation of the tinydhcp server
Overview A stack-based overflow vulnerability exists in the tinydhcp server in the Microchip Advanced Software Framework (ASF) that can lead to remote code execution. Description An implementation of DHCP in ASF fails input...
FortiClient – Lack of client-side certificate validation in ZTNA service
An improper certificate validation vulnerability [CWE-295] in FortiClientWindows, FortiClientLinux and FortiClientMac may allow a remote and unauthenticated attacker to perform a Man-in-the-Middle attack on the communication...
CISA Adds One Known Exploited Vulnerability to Catalog
CISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-8963 Ivanti Cloud Services Appliance (CSA) Path Traversal Vulnerability These types of...
Managing Cyber-Risk Is No Different Than Managing Any Business Risk
A sound cyber-risk management strategy analyzes all the business impacts that may stem from an...
Managing Cybersecurity and Privacy Risks in the Age of Artificial Intelligence: Launching a New Program at NIST
The rapid proliferation of Artificial Intelligence (AI) promises significant value for industry, consumers, and broader society, but as with many technologies, new risks from these advancements in AI must be managed to realize...
Ivanti Releases Admin Bypass Security Update for Cloud Services Appliance
Ivanti has released a security update to address an admin bypass vulnerability (CVE-2024-8963) affecting Ivanti Cloud Services Appliance (CSA) version 4.6. A cyber threat actor could exploit this vulnerability in conjunction...
23:59, Time to Exfiltrate!, (Tue, Sep 17th)
Last week, I posted a diary about suspicious Python modules. One of them was Firebase [1], the cloud service provided by Google[2]. Firebase services abused by attackers is not new, usually, it’s used to host malicious files...
Python Infostealer Patching Windows Exodus App, (Wed, Sep 18th)
A few months ago, I wrote a diary[1] about a Python script that replaced the Exodus[2] Wallet app...
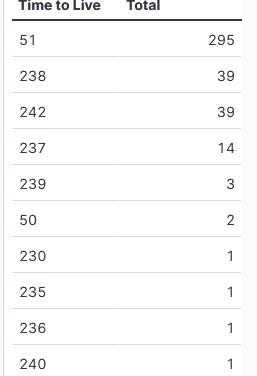
Time-to-Live Analysis of DShield Data with Vega-Lite, (Wed, Sep 18th)
Since posting a diary about Vega-Lite [1], I have “played” with other queries that...
BPL Medical Technologies PWS-01-BT and BPL Be Well Android Application
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 5.1 ATTENTION: Low attack complexity/public exploits are available Vendor: BPL Medical Technologies Equipment: PWS-01-BT, Be Well Android App Vulnerability: Cleartext Transmission of...
Google Chrome Switches to ML-KEM for Post-Quantum Cryptography Defense
Google has announced that it will be switching from KYBER to ML-KEM in its Chrome web browser as part of its ongoing efforts to defend against the risk posed by cryptographically relevant quantum computers (CRQCs). “Chrome...
2053 Advanced Mass Seminar
The 9-day, hands-on Advanced Mass calibration seminar focuses on the comprehension and application of the advanced mass dissemination procedures, the equations, and associated calculations. It includes the operation of the...
Russian Military Cyber Actors Target US and Global Critical Infrastructure
Summary The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security...
Rockwell Automation FactoryTalk View Site
View CSAF 1. EXECUTIVE SUMMARY CVSS v4 9.2 ATTENTION: Exploitable remotely/low attack complexity Vendor: Rockwell Automation Equipment: FactoryTalk Vulnerability: Command Injection 2. RISK EVALUATION Successful exploitation of...
access to backend information and logs via RestAPI on shared environments
An improper access control vulnerability [CWE-284] in FortiEDR Manager API may allow in a shared environment context an authenticated admin with REST API permissions in his profile and restricted to a specific organization to...
10 Writing Tips for Cybersecurity Professionals
It takes more than technical knowledge to write about cybersecurity in a way people want to read....
Learning, Sharing, and Exploring with NIST’s New Human-Centered Cybersecurity Community of Interest
Human-centered cybersecurity (also known as ‘usable security’) involves the social, organizational, and technological influences on people’s understanding of and interactions with cybersecurity. By taking a human-centered...
Attack Surface [Guest Diary], (Wed, Sep 4th)
[This is a Guest Diary by Joshua Tyrrell, an ISC intern as part of the SANS.edu BACS program] Managing the Attack Surface You’ve begun the journey of reviewing your IT infrastructure and attempting to figure out how to protect...
Enrichment Data: Keeping it Fresh, (Fri, Sep 6th)
I like to enrich my honeypot data from a variety of sources to help understand a bit more about...
North Korean Hackers Targets Job Seekers with Fake FreeConference App
North Korean threat actors have leveraged a fake Windows video conferencing application impersonating FreeConference.com to backdoor developer systems as part of an ongoing financially-driven campaign dubbed Contagious...

- 1
- ...
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
- 207
- 208
- 209
- 210
- 211
- 212
- 213
- 214
- 215
- 216
- 217
- 218
- 219
- 220
- 221
- 222
- 223
- 224
- 225
- 226
- 227
- 228
- 229
- 230
- 231
- 232
- 233
- 234
- 235
- 236
- 237
- 238
- 239
- 240
- 241
- 242
- 243
- 244
- 245
- 246
- 247
- 248
- 249
- 250
- 251
- 252
- 253
- 254
- 255
- 256
- 257
- 258
- 259
- 260
- 261
- 262
- 263
- 264
- 265
- 266
- 267
- 268
- 269
- 270
- 271
- 272
- 273
- 274
- 275
- 276
- 277
- 278
- 279
- 280
- 281
- 282
- 283
- 284
- 285
- 286
- 287
- 288
- 289
- 290
- 291
- 292
- 293
- 294
- 295
- 296
- 297
- 298
- 299
- 300
- 301
- 302
- 303
- 304
- 305
- 306
- 307
- 308
- 309
- 310
- 311
- 312
- 313
- 314
- 315
- 316
- 317
- 318
- 319
- 320
- 321
- 322
- 323
- 324
- 325
- 326
- 327
- 328
- 329
- 330
- 331
- 332
- 333
- 334
- 335
- 336
- 337
- 338
- 339
- 340
- 341
- 342
- 343
- 344
- 345
- 346
- 347
- 348
- 349
- 350
- 351
- 352
- 353
- 354
- 355
- 356
- 357
- 358
- 359
- 360
- 361
- 362
- 363
- 364
- 365
- 366
- 367
- 368
- 369
- 370
- 371
- 372
- 373
- 374
- 375
- 376
- 377
- 378
- 379
- 380
- 381
- 382
- 383
- 384
- 385
- 386
- 387
- 388
- 389
- 390
- 391
- 392
- 393
- 394
- 395
- 396
- 397
- 398
- 399
- 400
- 401
- 402
- 403
- 404
- 405
- 406
- 407
- 408
- 409
- 410
- 411
- 412
- 413
- 414
- 415
- 416
- 417
- 418
- 419
- 420
- 421
- 422
- 423
- 424
- 425
- 426
- 427
- 428
- 429
- 430
- 431
- 432
- 433
- 434
- 435
- 436
- 437
- 438
- 439
- 440
- 441
- 442
- 443
- 444
- 445
- 446
- 447
- 448
- 449
- 450
- 451
- 452
- 453
- 454
- 455
- 456
- 457
- 458
- 459
- 460
- 461
- 462
- 463
- 464
- 465
- 466
- 467
- 468
- 469
- 470
- 471
- 472
- 473
- 474
- 475
- 476
- 477
- 478
- 479
- 480
- 481
- 482
- 483
- 484
- 485
- 486
- 487
- 488
- 489
- 490
- 491
- 492
- 493
- 494
- 495
- 496
- 497
- 498
- 499
- 500
- 501
- 502
- 503
- 504
- 505
- 506
- 507
- 508
- 509
- 510
- 511
- 512
- 513
- 514
- 515
- 516
- 517
- 518
- 519
- 520
- 521
- 522
- 523
- 524
- 525
- 526
- 527
- 528
- 529
- 530
- 531
- 532
- 533
- 534
- 535
- 536
- 537
- 538
- 539
- 540
- 541
- 542
- 543
- 544
- 545
- 546
- 547
- 548
- 549
- 550
- 551
- 552
- 553
- 554
- 555
- 556
- 557
- 558
- 559
- 560
- 561
- 562
- 563
- 564
- 565
- 566
- 567
- 568
- 569
- 570
- 571
- 572
- 573
- 574
- 575
- 576
- 577
- 578
- 579
- 580
- 581
- 582
- 583
- 584
- 585
- 586
- 587
- 588
- 589
- 590
- 591
- 592
- 593
- 594
- 595
- 596
- 597
- 598
- 599
- 600
- 601
- 602
- 603
- 604
- 605
- 606
- 607
- 608
- 609
- 610
- 611
- 612
- 613
- 614
- 615
- 616
- 617
- 618
- 619
- 620
- 621
- 622
- 623
- 624
- 625
- 626
- 627
- 628
- 629
- 630
- 631
- 632
- 633
- 634
- 635
- 636
- 637
- 638
- 639
- 640
- 641
- 642
- 643
- 644
- 645
- 646
- 647
- 648
- 649
- 650
- 651
- 652
- 653
- 654
- 655
- 656
- 657
- 658
- 659
- 660
- 661
- 662
- 663
- 664
- 665
- 666
- 667
- 668
- 669
- 670
- 671
- 672
- 673
- 674
- 675
- 676
- 677
- 678
- 679
- 680
- 681
- 682
- 683
- 684
- 685
- 686
- 687
- 688
- 689
- 690
- 691
- 692
- 693
- 694
- 695
- 696
- 697
- 698
- 699
- 700
- 701
- 702
- 703
- 704
- 705
- 706
- 707
- 708
- 709
- 710
- 711
- 712
- 713
- 714
- 715
- 716
- 717
- 718
- 719
- 720
- 721
- 722
- 723
- 724
- 725
- 726
- 727
- 728
- 729
- 730
- 731
- 732
- 733
- 734
- 735
- 736
- 737
- 738
- 739
- 740
- 741
- 742
- 743
- 744
- 745
- 746
- 747
- 748
- 749
- 750
- 751
- 752
- 753
- 754
- 755
- 756
- 757
- 758
- 759
- 760
- 761
- 762
- 763
- 764
- 765
- 766
- 767
- 768
- 769
- 770
- 771
- 772
- 773
- 774
- 775
- 776
- 777
- 778
- 779
- 780
- 781
- 782
- 783
- 784
- 785
- 786
- 787
- 788
- 789
- 790
- 791
- 792
- 793
- 794
- 795
- 796
- 797
- 798
- 799
- 800
- 801
- 802
- 803
- 804
- 805
- 806
- 807
- 808
- 809
- 810
- 811
- 812
- 813
- 814
- 815
- 816
- 817
- 818
- 819
- 820
- 821
- 822
- 823
- 824
- 825
- 826
- 827
- 828
- 829
- 830
- 831
- 832
- 833
- 834
- 835
- 836
- 837
- 838
- 839
- 840
- 841
- 842
- 843
- 844
- 845
- 846
- 847
- 848
- 849
- 850
- 851
- 852
- 853
- 854
- 855
- 856
- 857
- 858
- 859
- 860
- 861
- 862
- 863
- 864
- 865
- 866
- 867
- 868
- 869
- 870
- 871
- 872
- 873
- 874
- 875
- 876
- 877
- 878
- 879
- 880
- 881
- 882
- 883
- 884
- 885
- 886
- 887
- 888
- 889
- 890
- 891
- 892
- 893
- 894
- 895
- 896
- 897
- 898
- 899
- 900
- 901
- 902
- 903
- 904
- 905
- 906
- 907
- 908
- 909
- 910
- 911
- 912
- 913
- 914
- 915
- 916
- 917
- 918
- 919
- 920
- 921
- 922
- 923
- 924
- 925
- 926
- 927
- 928
- 929
- 930
- 931
- 932
- 933
- 934
- 935
- 936
- 937
- 938
- 939
- 940
- 941
- 942
- 943
- 944
- 945
- 946
- 947
- 948
- 949
- 950
- 951
- 952
- 953
- 954
- 955
- 956
- 957
- 958
- 959
- 960
- 961
- 962
- 963
- 964
- 965
- 966
- 967
- 968
- 969
- 970
- 971
- 972
- 973
- 974
- 975
- 976
- 977
- 978
- 979
- 980
- 981
- 982
- 983
- 984
- 985
- 986
- 987
- 988
- 989
- 990
- 991
- 992
- 993
- 994
- 995
- 996
- 997
- 998
- 999
- 1000
- 1001
- 1002
- 1003
- 1004
- 1005
- 1006
- 1007
- 1008
- 1009
- 1010
- 1011
- 1012
- 1013
- 1014
- 1015
- 1016
- 1017
- 1018
- 1019
- 1020
- 1021
- 1022
- 1023
- 1024
- 1025
- 1026
- 1027
- 1028
- 1029
- 1030
- 1031
- 1032
- 1033
- 1034
- 1035
- 1036
- 1037
- 1038
- 1039
- 1040
- 1041
- 1042
- 1043
- 1044
- 1045
- 1046
- 1047
- 1048
- 1049
- 1050
- 1051
- 1052
- 1053
- 1054
- 1055
- 1056
- 1057
- 1058
- 1059
- 1060
- 1061
- 1062
- 1063
- 1064
- 1065
- 1066
- 1067
- 1068
- 1069
- 1070
- 1071
- 1072
- 1073
- 1074
- 1075
- 1076
- 1077
- 1078
- 1079
- 1080
- 1081
- 1082
- 1083
- 1084
- 1085
- 1086
- 1087
- 1088
- 1089
- 1090
- 1091
- 1092
- 1093
- 1094
- 1095
- 1096
- 1097
- 1098
- 1099
- 1100
- 1101
- 1102
- 1103
- 1104
- 1105
- 1106
- 1107
- 1108
- 1109
- 1110
- 1111
- 1112
- 1113
- 1114
- 1115
- 1116
- 1117
- 1118
- 1119
- 1120
- 1121
- 1122
- 1123
- 1124
- 1125
- 1126
- 1127
- 1128
- 1129
- 1130
- 1131
- 1132
- 1133
- 1134
- 1135
- 1136
- 1137
- 1138
- 1139
- 1140
- 1141
- 1142
- 1143
- 1144
- 1145
- 1146
- 1147
- 1148
- 1149
- 1150
- 1151
- 1152
- 1153
- 1154
- 1155
- 1156
- 1157
- 1158
- 1159
- 1160
- 1161
- 1162
- 1163
- 1164
- 1165
- 1166
- 1167
- 1168
- 1169
- 1170
- 1171
- 1172
- 1173
- 1174
- 1175
- 1176
- 1177
- 1178
- 1179
- 1180
- 1181
- 1182
- 1183
- 1184
- 1185
- 1186
- 1187
- 1188
- 1189
- 1190
- 1191
- 1192
- 1193
- 1194
- 1195
- 1196
- 1197
- 1198
- 1199
- 1200
- 1201
- 1202
- 1203
- 1204
- 1205
- 1206
- 1207
- 1208
- 1209
- 1210
- 1211
- 1212
- 1213
- 1214
- 1215
- 1216
- 1217
- 1218
- 1219
- 1220
- 1221
- 1222
- 1223
- 1224
- 1225
- 1226
- 1227
- 1228
- 1229
- 1230
- 1231
- 1232
- 1233
- 1234
- 1235
- 1236
- 1237
- 1238
- 1239
- 1240
- 1241
- 1242
- 1243
- 1244
- 1245
- 1246
- 1247
- 1248
- 1249
- 1250
- 1251
- 1252
- 1253
- 1254
- 1255
- 1256
- 1257
- 1258
- 1259
- 1260
- 1261
- 1262
- 1263
- 1264
- 1265
- 1266
- 1267
- 1268
- 1269
- 1270
- 1271
- 1272
- 1273
- 1274
- 1275
- 1276
- 1277
- 1278
- 1279
- 1280
- 1281
- 1282
- 1283
- 1284
- 1285
- 1286
- 1287
- 1288
- 1289
- 1290
- 1291
- 1292
- 1293
- 1294
- 1295
- 1296
- 1297
- 1298
- 1299
- 1300
- 1301
- 1302
- 1303
- 1304
- 1305
- 1306
- 1307
- 1308
- 1309
- 1310
- 1311
- 1312
- 1313
- 1314
- 1315
- 1316
- 1317
- 1318
- 1319
- 1320
- 1321
- 1322
- 1323
- 1324
- 1325
- 1326
- 1327
- 1328
- 1329
- 1330
- 1331
- 1332
- 1333
- 1334
- 1335
- 1336
- 1337
- 1338
- 1339
- 1340
- 1341
- 1342
- 1343
- 1344
- 1345
- 1346
- 1347
- 1348
- 1349
- 1350
- 1351
- 1352
- 1353
- 1354
- 1355
- 1356
- 1357
- 1358
- 1359
- 1360
- 1361
- 1362
- 1363
- 1364
- 1365
- 1366
- 1367
- 1368
- 1369
- 1370
- 1371
- 1372
- 1373
- 1374
- 1375
- 1376
- 1377
- 1378
- 1379
- 1380
- 1381
- 1382
- 1383
- 1384
- 1385
- 1386
- 1387
- 1388
- 1389
- 1390
- 1391
- 1392
- 1393
- 1394
- 1395
- 1396
- 1397
- 1398
- 1399
- 1400
- 1401
- 1402
- 1403
- 1404
- 1405
- 1406
- 1407
- 1408
- 1409
- 1410
- 1411
- 1412
- 1413
- 1414
- 1415
- 1416
- 1417
- 1418
- 1419
- 1420
- 1421
- 1422
- 1423
- 1424
- 1425
- 1426
- 1427
- 1428
- 1429
- 1430
- 1431
- 1432
- 1433
- 1434
- 1435
- 1436
- 1437
- 1438
- 1439
- 1440
- 1441
- 1442
- 1443
- 1444
- 1445
- 1446
- 1447
- 1448
- 1449
- 1450
- 1451
- 1452
- 1453
- 1454
- 1455
- 1456
- 1457
- 1458
- 1459
- 1460
- 1461
- 1462
- 1463
- 1464
- 1465
- 1466
- 1467
- 1468
- 1469
- 1470
- 1471
- 1472
- 1473
- 1474
- 1475
- 1476
- 1477
- 1478
- 1479
- 1480
- 1481
- 1482
- 1483
- 1484
- 1485
- 1486
- 1487
- 1488
- 1489
- 1490
- 1491
- 1492
- 1493
- 1494
- 1495
- 1496
- 1497
- 1498
- 1499
- 1500
- 1501
- 1502
- 1503
- 1504
- 1505
- 1506
- 1507
- 1508
- 1509
- 1510
- 1511
- 1512
- 1513
- 1514
- 1515
- 1516
- 1517
- 1518
- 1519
- 1520
- 1521
- 1522
- 1523
- 1524
- 1525
- 1526
- 1527
- 1528
- 1529
- 1530
- 1531
- 1532
- 1533
- 1534
- 1535
- 1536
- 1537
- 1538
- 1539
- 1540
- 1541
- 1542
- 1543
- 1544
- 1545
- 1546
- 1547
- 1548
- 1549
- 1550
- 1551
- 1552
- 1553
- 1554
- 1555
- 1556
- 1557
- 1558
- 1559
- 1560
- 1561
- 1562
- 1563
- 1564
- 1565
- 1566
- 1567
- 1568
- 1569
- 1570
- 1571
- 1572
- 1573
- 1574
- 1575
- 1576
- 1577
- 1578
- 1579
- 1580
- 1581
- 1582
- 1583
- 1584
- 1585
- 1586
- 1587
- 1588
- 1589
- 1590
- 1591
- 1592
- 1593
- 1594
- 1595
- 1596
- 1597
- 1598
- 1599
- 1600
- 1601
- 1602
- 1603
- 1604
- 1605
- 1606
- 1607
- 1608
- 1609
- 1610
- 1611
- 1612
- 1613
- 1614
- 1615
- 1616
- 1617
- 1618
- 1619
- 1620
- 1621
- 1622
- 1623
- 1624
- 1625
- 1626
- 1627
- 1628
- 1629
- 1630
- 1631
- 1632
- 1633
- 1634
- 1635
- 1636
- 1637
- 1638
- 1639
- 1640
- 1641
- 1642
- 1643
- 1644
- 1645
- 1646
- 1647
- 1648
- 1649
- 1650
- 1651
- 1652
- 1653
- 1654
- 1655
- 1656
- 1657
- 1658
- 1659
- 1660
- 1661
- 1662
- 1663
- 1664
- 1665
- 1666
- 1667
- 1668
- 1669
- 1670
- 1671
- 1672
- 1673
- 1674
- 1675
- 1676
- 1677
- 1678
- 1679
- 1680
- 1681
- 1682
- 1683
- 1684
- 1685
- 1686
- 1687
- 1688
- 1689
- 1690
- 1691
- 1692
- 1693
- 1694
- 1695
- 1696
- 1697
- 1698
- 1699
- 1700
- 1701
- 1702
- 1703
- 1704
- 1705
- 1706
- 1707
- 1708
- 1709
- 1710
- 1711
- 1712
- 1713
- 1714
- 1715
- 1716
- 1717
- 1718
- 1719
- 1720
- 1721
- 1722
- 1723
- 1724
- 1725
- 1726
- 1727
- 1728
- 1729
- 1730
- 1731
- 1732
- 1733
- 1734
- 1735
- 1736
- 1737
- 1738
- 1739
- 1740
- 1741
- 1742
- 1743
- 1744
- 1745
- 1746
- 1747
- 1748
- 1749
- 1750
- 1751
- 1752
- 1753
- 1754
- 1755
- 1756
- 1757
- 1758
- 1759
- 1760
- 1761
- 1762
- 1763
- 1764
- 1765
- 1766
- 1767
- 1768
- 1769
- 1770
- 1771
- 1772
- 1773
- 1774
- 1775
- 1776
- 1777
- 1778
- 1779
- 1780
- 1781
- 1782
- 1783
- 1784
- 1785
- 1786
- 1787
- 1788
- 1789
- 1790
- 1791
- 1792
- 1793
- 1794
- 1795
- 1796
- 1797
- 1798
- 1799
- 1800
- 1801
- 1802
- 1803
- 1804
- 1805
- 1806
- 1807
- 1808
- 1809
- 1810
- 1811
- 1812
- 1813
- 1814
- 1815
- 1816
- 1817
- 1818
- 1819
- 1820
- 1821
- 1822
- 1823
- 1824
- 1825
- 1826
- 1827
- 1828
- 1829
- 1830
- 1831
- 1832
- 1833
- 1834
- 1835
- 1836
- 1837
- 1838
- 1839
- 1840
- 1841
- 1842
- 1843
- 1844
- 1845
- 1846
- 1847
- 1848
- 1849
- 1850
- 1851
- 1852
- 1853
- 1854
- 1855
- 1856
- 1857
- 1858
- 1859
- 1860
- 1861
- 1862
- 1863
- 1864
- 1865
- 1866
- 1867
- 1868
- 1869
- 1870
- 1871
- 1872
- 1873
- 1874
- 1875
- 1876
- 1877
- 1878
- 1879
- 1880
- 1881
- 1882
- 1883
- 1884
- 1885
- 1886
- 1887
- 1888
- 1889
- 1890
- 1891
- 1892
- 1893
- 1894
- 1895
- 1896
- 1897
- 1898
- 1899
- 1900
- 1901
- 1902
- 1903
- 1904
- 1905
- 1906
- 1907
- 1908
- 1909
- 1910
- 1911
- 1912
- 1913
- 1914
- 1915
- 1916
- 1917
- 1918
- 1919
- 1920
- 1921
- 1922
- 1923
- 1924
- 1925
- 1926
- 1927
- 1928
- 1929
- 1930
- 1931
- 1932
- 1933
- 1934
- 1935
- 1936
- 1937
- 1938
- 1939
- 1940
- 1941
- 1942
- 1943
- 1944
- 1945
- 1946
- 1947
- 1948
- 1949
- 1950
- 1951
- 1952
- 1953
- 1954
- 1955
- 1956
- 1957
- 1958
- 1959
- 1960
- 1961
- 1962
- 1963
- 1964
- 1965
- 1966
- 1967
- 1968
- 1969
- 1970
- 1971
- 1972
- 1973
- 1974
- 1975
- 1976
- 1977
- 1978
- 1979
- 1980
- 1981
- 1982
- 1983
- 1984
- 1985
- 1986
- 1987
- 1988
- 1989
- 1990
- 1991
- 1992
- 1993
- 1994
- 1995
- 1996
- 1997
- 1998
- 1999
- 2000
- 2001
- 2002
- 2003
- 2004
- 2005
- 2006
- 2007
- 2008
- 2009
- 2010
- 2011
- 2012
- 2013
- 2014
- 2015
- 2016
- 2017
- 2018
- 2019
- 2020
- 2021
- 2022
- 2023
- 2024
- 2025
- 2026
- 2027
- 2028
- 2029
- 2030
- 2031
- 2032
- 2033
- 2034
- 2035
- 2036
- 2037
- 2038
- 2039
- 2040
- 2041
- 2042
- 2043
- 2044
- 2045
- 2046
- 2047
- 2048
- 2049
- 2050
- 2051
- 2052
- 2053
- 2054
- 2055
- 2056
- 2057
- 2058
- 2059
- 2060
- 2061
- 2062
- 2063
- 2064
- 2065
- 2066
- 2067
- 2068
- 2069
- 2070
- 2071
- 2072
- 2073
- 2074
- 2075
- 2076
- 2077
- 2078
- 2079
- 2080
- 2081
- 2082
- 2083
- 2084
- 2085
- 2086
- 2087
- 2088
- 2089
- 2090
- 2091
- 2092
- 2093
- 2094
- 2095
- 2096
- 2097
- 2098
- 2099
- 2100
- 2101
- 2102
- 2103
- 2104
- 2105
- 2106
- 2107
- 2108
- 2109
- 2110
- 2111
- 2112
- 2113
- 2114
- 2115
- 2116
- 2117
- 2118
- 2119
- 2120
- 2121
- 2122
- 2123
- 2124
- 2125
- 2126
- 2127
- 2128
- 2129
- 2130
- 2131
- 2132
- 2133
- 2134
- 2135
- 2136
- 2137
- 2138
- 2139
- 2140
- 2141
- 2142
- 2143
- 2144
- 2145
- 2146
- 2147
- 2148
- 2149
- 2150
- 2151
- 2152
- 2153
- 2154
- 2155
- 2156
- 2157
- 2158
- 2159
- 2160
- 2161
- 2162
- 2163
- 2164
- 2165
- 2166
- 2167
- 2168
- 2169
- 2170
- 2171
- 2172
- 2173
- 2174
- 2175
- 2176
- 2177
- 2178
- 2179
- 2180
- 2181
- 2182
- 2183
- 2184
- 2185
- 2186
- 2187
- 2188
- 2189
- 2190
- 2191
- 2192
- 2193
- 2194
- 2195
- 2196
- 2197
- 2198
- 2199
- 2200
- 2201
- 2202
- 2203
- 2204
- 2205
- 2206
- 2207
- 2208
- 2209
- 2210
- 2211
- 2212
- 2213
- 2214
- 2215
- 2216
- 2217
- 2218
- 2219
- 2220
- 2221
- 2222
- 2223
- 2224
- 2225
- 2226
- 2227
- 2228
- 2229
- 2230
- 2231
- 2232
- 2233
- 2234
- 2235
- 2236
- 2237
- 2238
- 2239
- 2240
- 2241
- 2242
- 2243
- 2244
- 2245
- 2246
- 2247
- 2248
- 2249
- 2250
- 2251
- 2252
- 2253
- 2254
- 2255
- 2256
- 2257
- 2258
- 2259
- 2260
- 2261
- 2262
- 2263
- 2264
- 2265
- 2266
- 2267
- 2268
- 2269
- 2270
- 2271
- 2272
- 2273
- 2274
- 2275
- 2276
- 2277
- 2278
- 2279
- 2280
- 2281
- 2282
- 2283
- 2284
- 2285
- 2286
- 2287
- 2288
- 2289
- 2290
- 2291
- 2292
- 2293
- 2294
- 2295
- 2296
- 2297
- 2298
- 2299
- 2300
- 2301
- 2302
- 2303
- 2304
- 2305
- 2306
- 2307
- 2308
- 2309
- 2310
- 2311
- 2312
- 2313
- 2314
- 2315
- 2316
- 2317
- 2318
- 2319
- 2320
- 2321
- 2322
- 2323
- 2324
- 2325
- 2326
- 2327
- 2328
- 2329
- 2330
- 2331
- 2332
- 2333
- 2334
- 2335
- 2336
- 2337
- 2338
- 2339
- 2340
- 2341
- 2342
- 2343
- 2344
- 2345
- 2346
- 2347
- 2348
- 2349
- 2350
- 2351
- 2352
- ...
- 2353