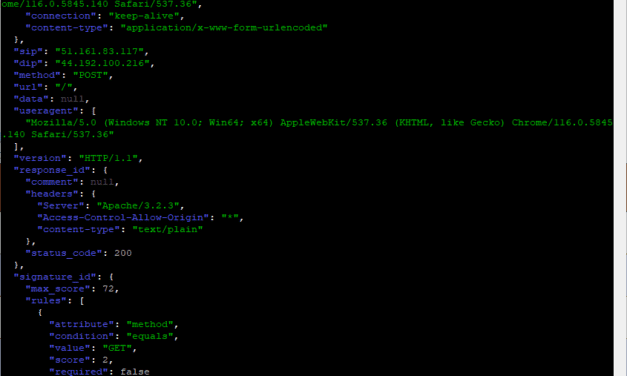
More SSH Fun!, (Tue, Dec 24th)
A few days ago, I wrote a diary[1] about a link file that abused the ssh.exe tool present in modern versions of Microsoft Windows. At the end, I mentioned that I will hunt for more SSH-related files/scripts. Guess what? I...
Read More