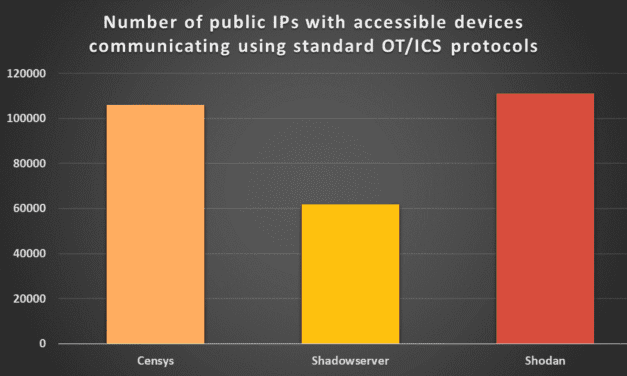
It appears that the number of industrial devices accessible from the internet has risen by 30 thousand over the past three years, (Mon, Apr 22nd)
LinkedIn It has been nearly three years since we last looked at the number of industrial devices...
Read More


![A Use Case for Adding Threat Hunting to Your Security Operations Team. Detecting Adversaries Abusing Legitimate Tools in A Customer Environment. [Guest Diary], (Sun, Apr 7th)](https://b923496.smushcdn.com/923496/wp-content/uploads/2024/04/Nathaniel_Jakusz_pic1-374x376.png?lossy=1&strip=1&webp=1)